Since we run multiple filters at work that do a good job that block spam and malware infested email, I am always interested in what makes it through the defenses as opportunites for improvement.
Take, for instance, an email I received tonight about a supposed order I made.
What did I order?
Hmmmm...I ordered something today with my VISA with email containing my email from a .ru email address (for those not familiar, .ru is Russia). They are so kind to send me an invoice of my order in an attachment, which happens to be a .html file (web page code, again if you are not familiar).
Looks legit to me. :)
Okay. I know, suspicious file....must send it over to virustotal.com and see if it detects anything in the file.
No viruses detected???
Suspicious email, suspicious attachment, but comes up clean...what gives?
Let's open up the html code in a text editor and see what is going on....
Cyrillic plus mysterious javascript...
Fortunately, we have other tools to try to get a better handle of what is going on. Submitting the file to malwr.com (run by the ShadowServer folks), we see there is really more than meets the eye.
Creates server and adds to startup....
There is definitely something malicious about this email. Time to throw it into a virtual machine and try to analyze safely. In my linux machine, opening the .html file opens this up....
Rut Roh.....
Double extensions....PDF to make the end user believe he is downloading a copy of the invoice to read in Adobe, but is it? .scr extensions are often used for Screen Savers in the Windows world, or as an extension for a script.
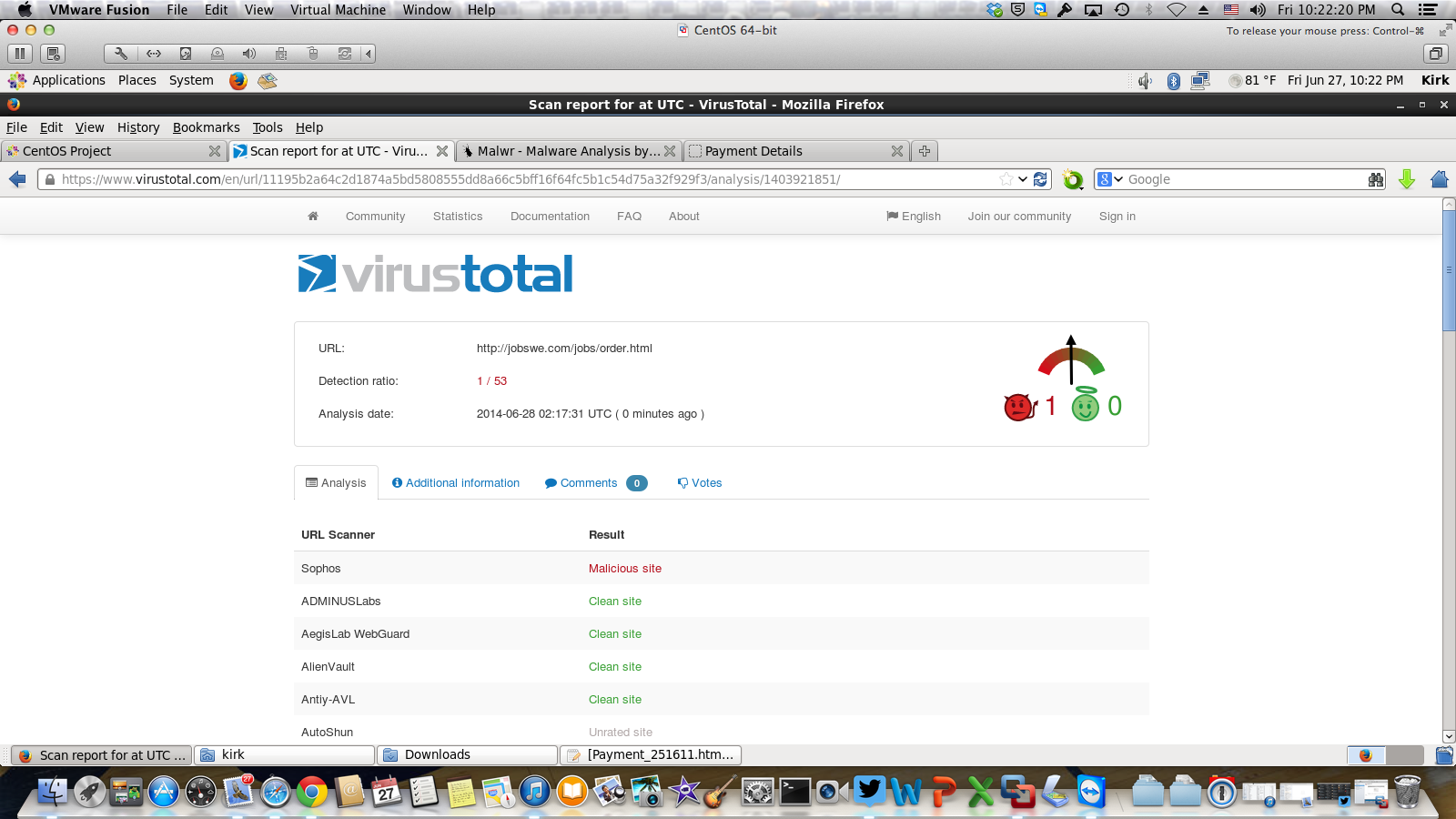
Let's pop the URL that we downloaded the file from and see if protection is up to date?
Only one URL scanner showing this as malicious
Moral of the story is if it waddles like a duck and quacks like a duck, it is probably a duck, and this duck will make your system sick. Never click on unexpected attachments or links in email without verifying from source.
If you have questions about a file, don't hesitate to use tools like VirusTotal and Malwr for them to analyze and help security companies improve their tools with malware samples.